▼
In order to sync an iPhone running iOS 7 with your Mac you need to run iTunes 11.1. The combination of MacOS 10.9, iTunes 11.1 and iOS 7 will no longer sync calendars and contacts between a Mac and an iOS device directly over USB or Wi-Fi: the only way to do this is using iCloud or other CalDAV and CardDAV servers.
For contacts that didn't bother me too much, although it's still enormously annoying that Apple takes away useful features like this whenever they feel like it. With no advance warning either. But for contacts, this created a problem for me. It's probably a bit irrational, but I really don't want to give my contact list to Apple/iCloud. (And certainly not Whatsapp/Facebook, which leaves Whatsapp only barely usable because you then only see phone numbers.)
Like I said, it's probably somewhat irrational, because my contact info is in other people's contact lists, so Apple, Facebook, the NSA and everyone else already has all this info anyway. However, the trouble with contacts is that unlike calendars, you really need to sync all of them entirely to be useful.
In any event, the good news is that as of MacOS 10.9.3 and iTunes 11.2, it's again possible to sync contacts using the USB cable or over Wi-Fi:
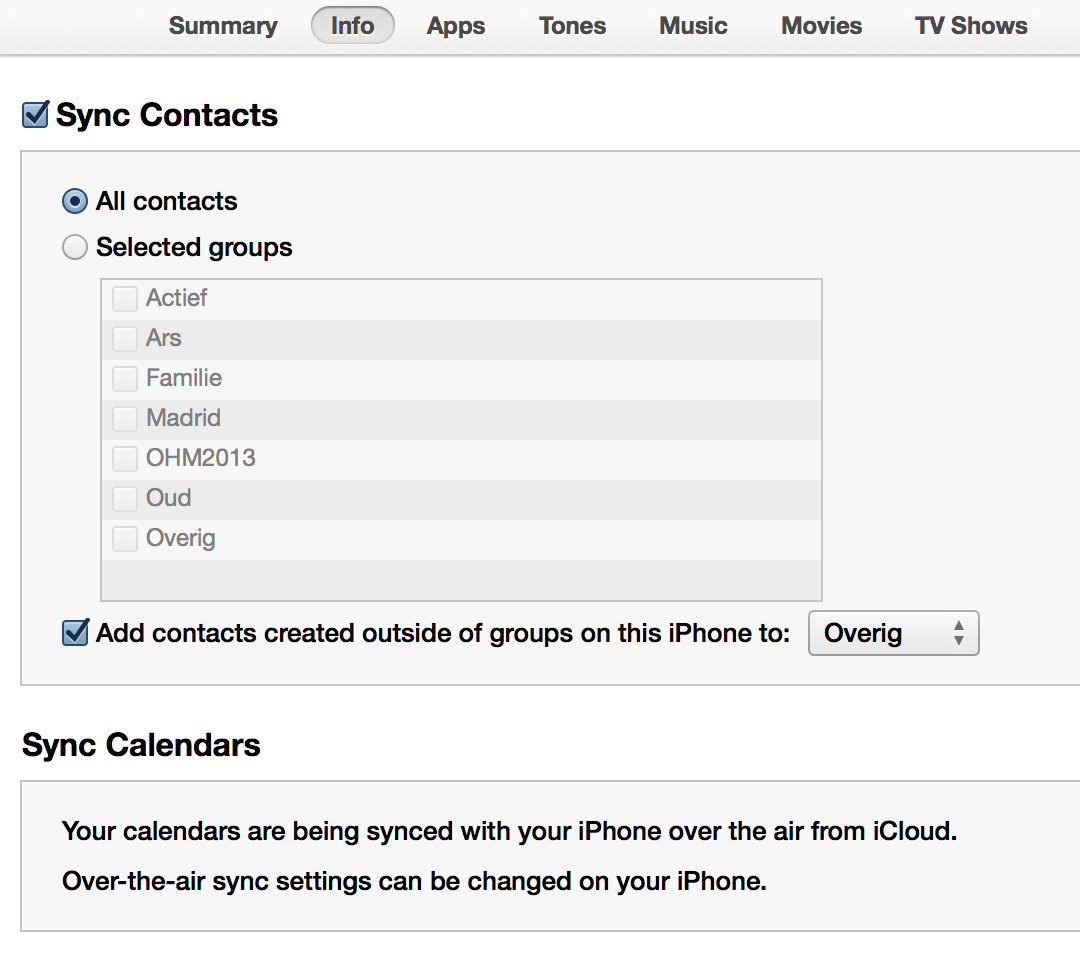
Unfortunately, syncing contacts with iPods remains missing in action, and syncing calendars also wasn't brought back.
There are also some interesting changes to podcasting in iTunes 11.2, which finally fixes the long-standing bug where manually downloaded podcasts wouldn't be deleted automatically after they had been played. And the Podcasts application on the iPhone now gains Siri integration in version 2.1, and also lists more episodes per screen and improves support for shownotes (tap on the album art during playback).
Permalink - posted 2014-05-20
Good piece on the misguided efforts to get adults to wear helmets when riding a bicycle.
Here in Holland adults on regular bikes (as opposed to racing bikes) virtually never wear helmets. I've never heard of anyone falling off of their bikes on their heads.
I've cycled 8000 km last year myself, and I can think of very many things that would make the roads safer for cycling, the first of which would be to, you know, look at the traffic around you. Helmets would be very far down the list.
I got some flack for always listening to podcasts or music when cycling, but I don't think that's a problem. I keep the volume low enough that I can still hear car horns and I'm very careful about looking in all directions, including behind me, which many cyclists don't. I had two minor collisions the past year, in both cases because another cyclist turned left unexpectedly as I was passing them.
Permalink - posted 2014-05-20
I started taking photos in the 1980s. I still have a bunch of black-and-white negatives that I developed myself, but never got them printed. In addition to that, I have color photos with their negatives and slides. The past years, I've been looking for a way to digitize all of these. The number of photos isn't huge, maybe a few hundred, but having a service do it at 50 cents or so quickly adds up. Turns out that some flatbed scanners have a transparency attachment so you can scan negatives and slides. The Epson Perfection V370 Photo scanner has a transparency mode built in. It gets pretty good reviews and only costs about € 80 or $100. So I got one.
▼
The other day I had a discussion about whether to use the "standard" sRGB color space or a larger color space for my digital photos. My thinking was that because my monitors are limited to sRGB (or less) anyway, I'm not going to see any colors that fall outside what an sRGB file can encode. So there's no immediate need to use a bigger color space such as Adobe RGB 1998. Here's the same photo taken with my Nikon D7100, the left one using sRGB and the right one using Adobe RGB 1998 (they are mousoverable):


(If you have a screen that doesn't do better than sRGB and your browser and operating system do proper color management, the colors in the two photos should look identical. If the right one looks duller, your software doesn't do proper color management. If your screen is better than sRGB and your software does proper color management, the colors in the photo on the right should look more saturated.)
(I actually had a hard time making sure the files are really different. They are. Use Firefox and the setting gfx.color_management.mode = 0 in about:config as explained here, restart Firefox, load this page and you'll see.)
I could of course use Adobe RGB anyway in anticipation of better hardware in the future. The trouble is that not all hard- and software uses color management properly. If something along the way then interprets an Adobe RGB file as an sRGB file, the results will be worse.
Anyway, I then looked at what the JPEG and raw files that come out of the camera look like. The camera can record more color information than what can be stored in a file that uses an sRGB color profile, so when creating an sRGB JPEG file, the camera must reduce the color gamut somehow. The camera can also produce raw files, which is basically a dump of the data straight from the image sensor. Preview, Apple's image viewing/conversion tool, interprets those files as Adobe RGB 1998, but then of course also has to reduce the color gamut in order to display the file. And it does that very differently from how Nikon does it:

So it looks like Nikon just dials down the saturation of the colors, while Apple "clips" the very saturated colors that fall outside the sRGB color space. It's hard to say which approach is superior, but they are very different.
Permalink - posted 2014-05-04





